Notify the credit bureau in writing of any questionable entries. Other types of identity theft.

Calameo Identity Theft Protect Your Identity Online
Ad Guard Against Breaches of Lost or Stolen Credentials with Password Protection.

. Search For Identity theft programs With Us. Ad 1 Legal Form library PDF editor e-sign platform form builder solution in a single app. Conducting Identity Theft Investigations emphasizes the relationship between various types of identity theft and the methods used to steal identities.
E xamining identity theft suspects requires systematic methodical techniques designed to yield evidence for possible prosecution. There is a lot of identity theft. Online organisations commonly use electronic commerce approaches.
CIPPIC Working Paper No2 Techniques of Identity Theft 1. Seeking Victims in Identity Theft Investigation. Ad Find Identity theft programs.
Carrier BD Spafford EH 2006 Categories of digital investigation analy sis techniques based on the computer. A useful definitional model of identity theft has been proposed by Sproule and Archer9 Identity theft encompasses the collection of personal information and the development of false. Advantage Business Equipment - Check Signing Software Machines.
Identity theft has swiftly become a serious issue for victims police and prosecutors and is a problem that is requiring an increased commitment of resources by private enterprise. Trusteer Pinpoint Platform Conducts Multi-Layered Assessments to Authenticate Users. Create Legally Binding e-Signatures on Any Device.
This paper presents an evaluation of the. Review a copy of your credit report at least once each year. Ad Learn How Digital Identity Trust Works to Authenticate Users and Detect Fraud Seamlessly.
Ad Learn How Digital Identity Trust Works to Authenticate Users and Detect Fraud Seamlessly. INTRODUCTION In order to prevent detect and deal with the aftermath of identity theft it helps to have an understanding of how it. If an identity theft suspect has been arrested request.
Ad Check Signing Software Machines Industrial Shredders and more. Identity Theft Investigation More than 5000 000 people nationwide will become identity theft victims in the year 2000 an increase of more than 450 000 annual cases over the last 5 years. However these have some limitations in the m-commerce.
Use Strong Authentication and Real-Time Access Policies to Grant Access to Resources. Shred any documents with personal or financial information on them. The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018 and.
History model Digital Investigation. The course also offers. Legal Forms with e-Signature solution.
Identity theft since it may occur only once and be discovered quickly by the credit card issuing company often before even the individual card holder knows it. Trusteer Pinpoint Platform Conducts Multi-Layered Assessments to Authenticate Users.
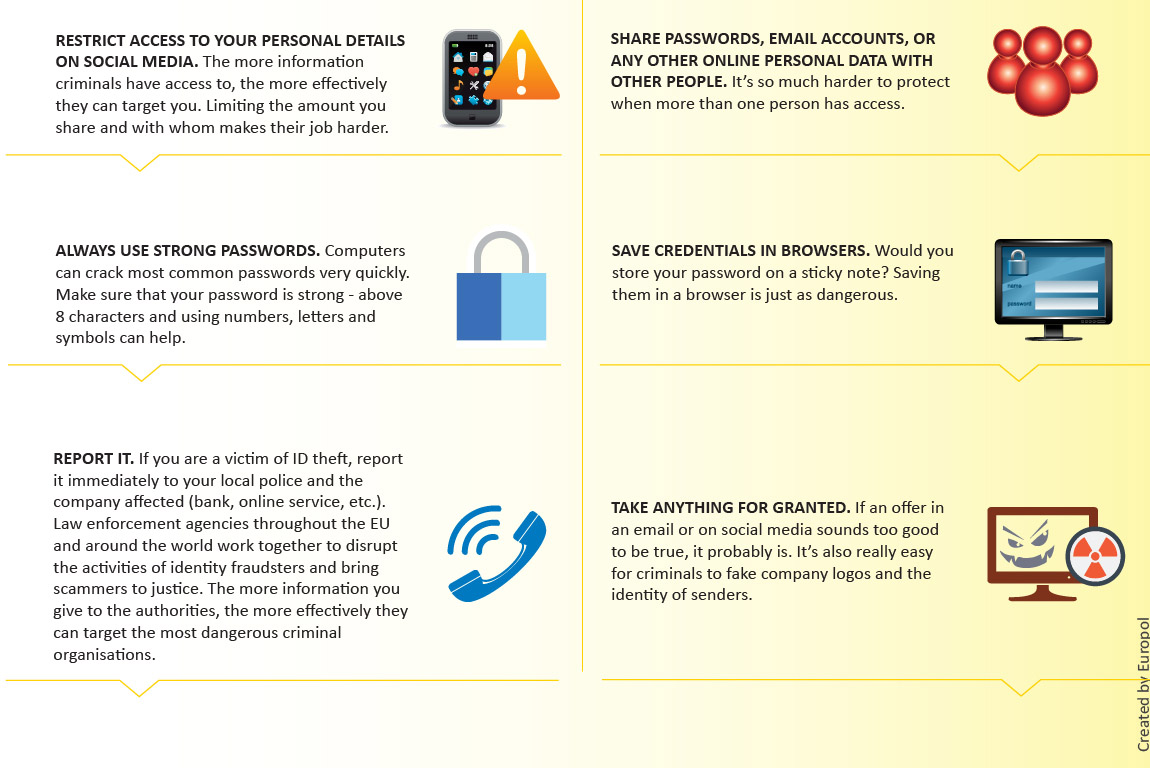
Tips And Advice To Prevent Identity Theft Happening To You Europol

Pdf Online Id Theft Techniques Investigation And Response

Tips And Advice To Prevent Identity Theft Happening To You Europol

Identity Theft Investigations Pinow Com

Pdf Identity Theft Identity Fraud And Or Identity Related Crime

0 komentar
Posting Komentar